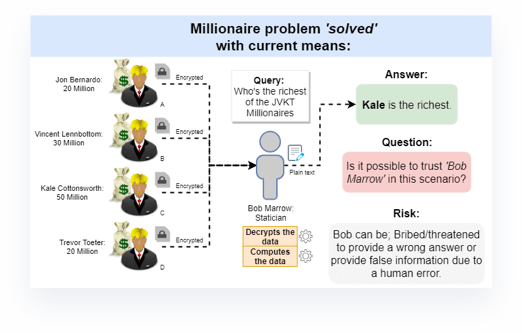
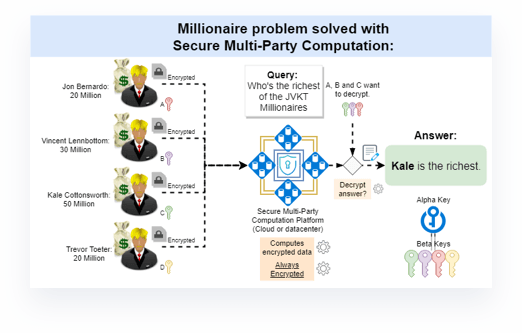
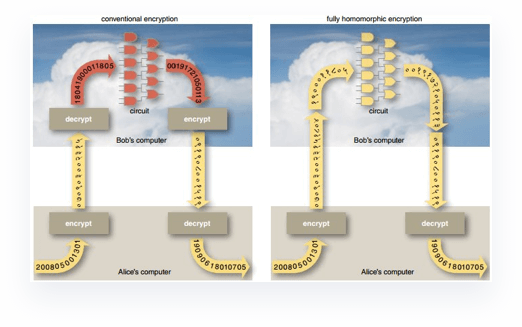
Traditional scenario of the 'Millionaire problem':
Let's say there are 5 individuals named Jon, Vincent, Kale, Trevor and Bob. Jon, Vincent, Kale and Trevor (JVKT for short) are all millionaires and live a wealthy life. The JVKT millionaires are rather rich but don't know who's the richest of them all. However, they don't want to show each other how much they each specifically have. That's where Bob comes in. Let's say Bob is incorruptable and therefore unbribable and will always supply the correct answer and never leak data. Learn More